The $120,000 Wake-Up Call: When “Too Small to Target” Becomes “Too Costly to Survive”
A 75-employee architecture firm in Chicago loses access to all client files, project blueprints, and financial records on a Tuesday morning. By Friday, they’ve paid $35,000 in ransom, lost three major clients, and face another $85,000 in recovery costs. Sound extreme? It’s the new reality. The average cost of a small business data breach in 2025 is $120,000, while 60% of small businesses that experience a cyber attack go out of business within 6 months.
Here’s the shocking truth: 43% of cyber attacks target small businesses, yet 51% of small businesses have no cybersecurity measures in place at all. If you’re managing 50+ employees, you’re not “too small” to be a target-you’re the perfect size for cybercriminals looking for easy wins.
The Basics: Encryption in Your Office
Think of Encryption as Your Digital Mailroom Security System
Imagine your office mailroom where sensitive documents are sorted and distributed. Without encryption, it’s like having all your confidential files spread across open desks where anyone walking by can read them. With encryption, those same documents are locked in secure envelopes that only authorized recipients can open.
Encryption Protects Your Daily Operations:
- Email Communications: Every client proposal, contract, and internal memo
- File Storage: Customer databases, financial records, and employee information
- Payment Systems: Credit card processing and banking transactions
- Cloud Documents: Shared folders, project files, and backup systems
Visual Comparison: Unencrypted vs. Encrypted Data
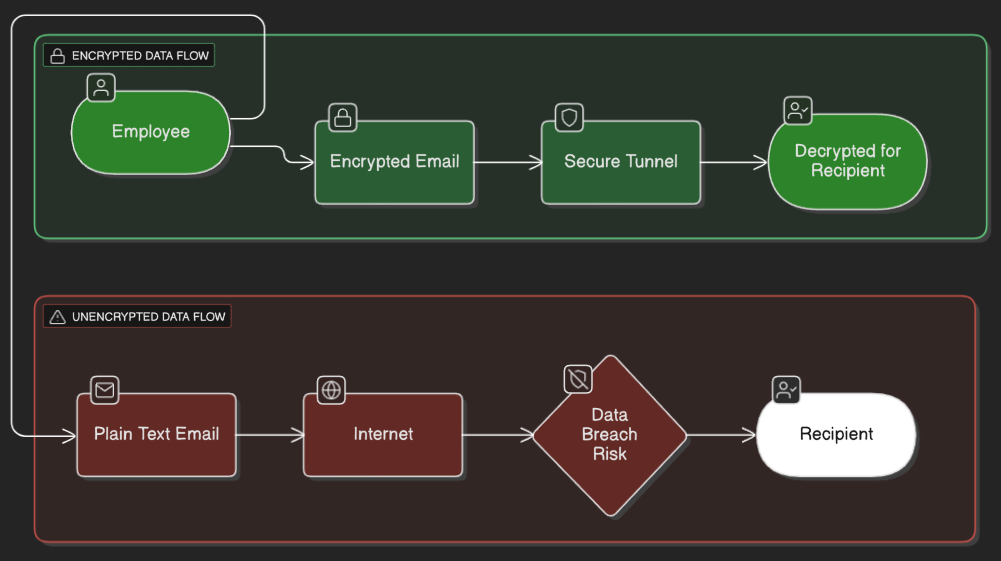
Real-World Impact: According to IBM’s 2025 report, organizations that extensively use AI and encryption in security experience $1.8 million in cost savings compared to those that don’t. For a mid-sized company, that’s the difference between surviving an attack and closing permanently.
Common Encryption Touchpoints in Your Office:
- WiFi networks (WPA3 encryption)
- Email platforms (TLS encryption)
- File sharing services (AES-256 encryption)
- Payment processing (SSL/TLS encryption)
- Remote access tools (VPN encryption)
The key insight: encryption isn’t a luxury-it’s your first line of defense in an environment where small businesses face cyber attacks every 11 seconds.
Essential Security Measures
Password Management: Building Digital Fort Knox
The Problem: 80% of all hacking incidents involve compromised credentials, yet 63% of small business employees reuse passwords across multiple platforms.
Sample Policy Framework:
- Minimum 12 characters with mixed case, numbers, symbols
- Unique passwords for each system/account
- Mandatory password manager for all employees
- 90-day rotation for administrative accounts
Timeline: 2-4 weeks for full deployment and training
Data Transmission Security: Your Digital Bank Transfer System
Think of secure data transmission like bank wire transfers-multiple verification steps, encrypted channels, and audit trails. Just as banks don’t send money through unsecured channels, your business data needs the same protection.
Key Implementations:
- Email Encryption: Microsoft 365 E3 with encryption ($22/user/month)
- VPN Access: Secure remote connections ($5-15/user/month)
- File Transfer: Encrypted document sharing platforms ($10-25/user/month)
ROI Example: A 50-employee firm spending $2,500/month on transmission security avoids the average $120,000 breach cost-paying for itself in just 2 years.
Access Control: Your Digital Building Security System
Multi-Factor Authentication (MFA): Installing MFA reduces phishing attacks by 90%.
Three-Tier Access Structure:
- Basic Users: Email, file sharing, standard applications
- Department Heads: Financial systems, customer databases, project management
- Administrators: Full system access, security settings, user management
Implementation Timeline Sidebar:
- Week 1-2: Password manager rollout and training
- Week 3-4: MFA implementation across all systems
- Week 5-6: Access control review and permission cleanup
- Week 7-8: Employee training and policy documentation
- Week 9-12: Monitoring and refinement period
Action Steps for Managers
Three-Month Implementation Roadmap
Month 1: Foundation Building
- Week 1: Security assessment and current state analysis
- Week 2: Select and purchase password management solution
- Week 3: Deploy password manager to all employees
- Week 4: Implement MFA on email and critical systems
Month 2: System Hardening
- Week 5-6: Set up VPN access for remote workers
- Week 7: Configure email encryption and secure file sharing
- Week 8: Conduct access control audit and cleanup
Month 3: Training and Refinement
- Week 9-10: Comprehensive cybersecurity training program
- Week 11: Test incident response procedures
- Week 12: Review, document, and refine all policies
Employee Training Outline
- Phishing Identification Workshop (2 hours)
- Real-world email examples and red flags
- Hands-on simulation exercises
- Password Security Masterclass (1 hour)
- Password manager demonstration and setup
- Incident Response Protocol (1 hour)
- Who to contact, what to document, immediate steps
Vendor Evaluation Criteria
- Compliance certifications (SOC 2, ISO 27001)
- 24/7 support availability and response times
- Integration capabilities with existing systems
- Scalability for business growth
- Cost transparency and contract flexibility
- References from similar-sized businesses
- Data residency and privacy protections
Your Cybersecurity Investment: The Bottom Line
The math is simple: investing $15,000-25,000 annually in comprehensive cybersecurity for a 50-employee office costs significantly less than the average $120,000 breach. More importantly, 75% of small businesses that experienced cyber attacks report they could not continue operating if hit with a ransomware attack. Could you?
Cost-Benefit Snapshot:
- Annual Investment (Avg): $18,000 (comprehensive security for 50 employees)
- Average Breach Cost: $120,000 + potential business closure
- ROI: 85% risk reduction for less than 15% of potential loss
Key Takeaways:
- Encryption and access controls are non-negotiable basics
- Employee training reduces incidents by 70%
- Incremental implementation over 3 months minimizes business disruption
- The cost of prevention is always less than the cost of recovery
Trusted Resources:
- NIST Cybersecurity Framework – Free implementation guide
- CISA Small Business Resources – Government cybersecurity tools
- IBM Cost of Data Breach Report 2025 – Annual threat landscape analysis
Next Step: Contact US to schedule a cybersecurity assessment within 30 days-the threat landscape won’t wait for your convenience.